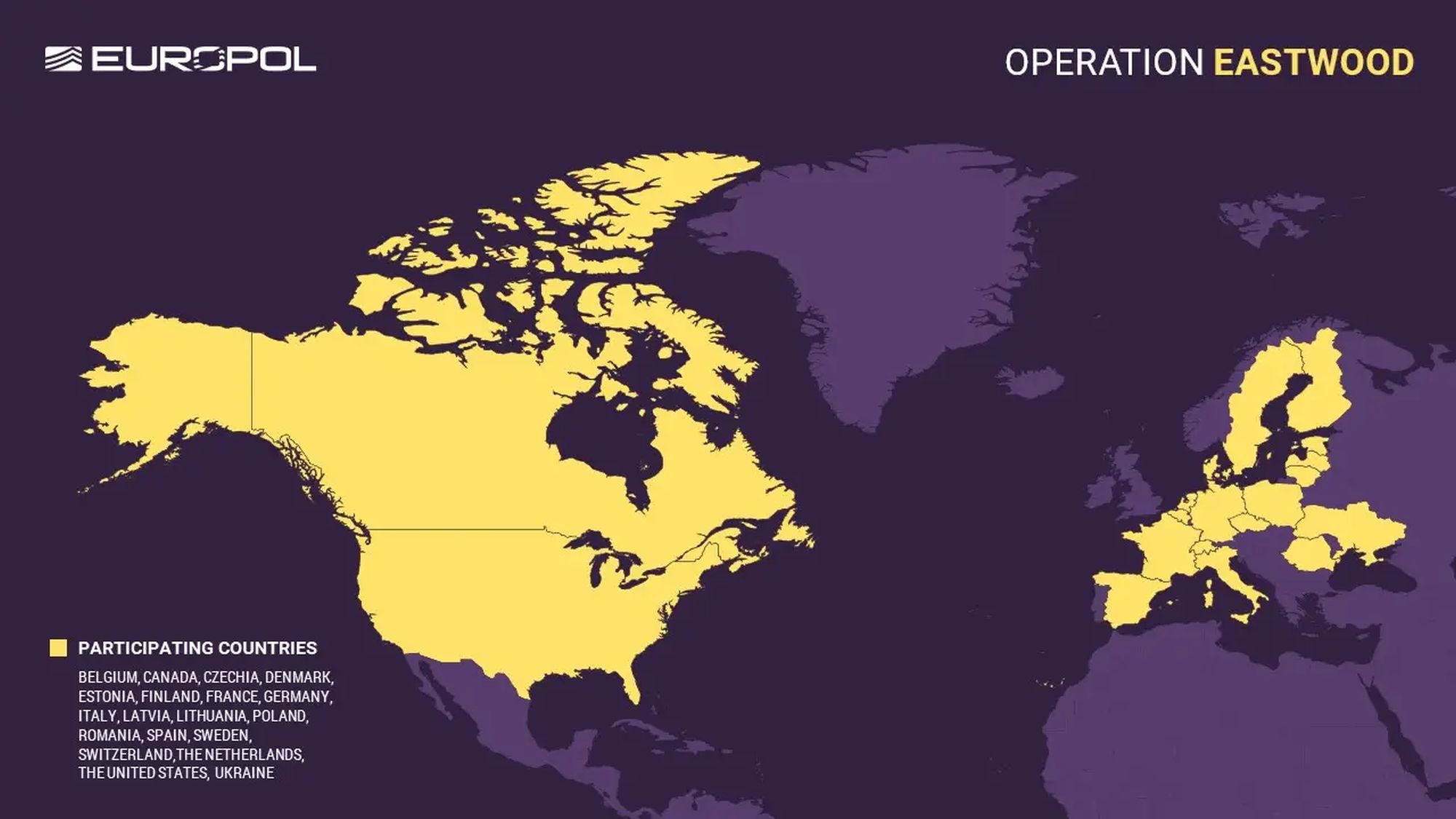
As part of a large-scale coordinated operation "Eastwood" law enforcement authorities from respective countries, including Poland, hit the pro-Russian cybercrime group NoName057(16).
Actions led to arrests, searches and the liquidation of a key part of hacker infrastructure that attacked Ukraine and supporting its countries.
The global action, coordinated by Europol and Eurojust, began on 14 July. It was attended by services from the Czech Republic, Finland, France, Germany, Italy, Lithuania, Poland, Spain, Sweden, Switzerland, the Netherlands and the United States. The goal was group NoName057(16), known for conducting DDoS attacks (distributed refusal of service), motivated ideologically and aimed at countries supporting Ukraine in the war against Russia.
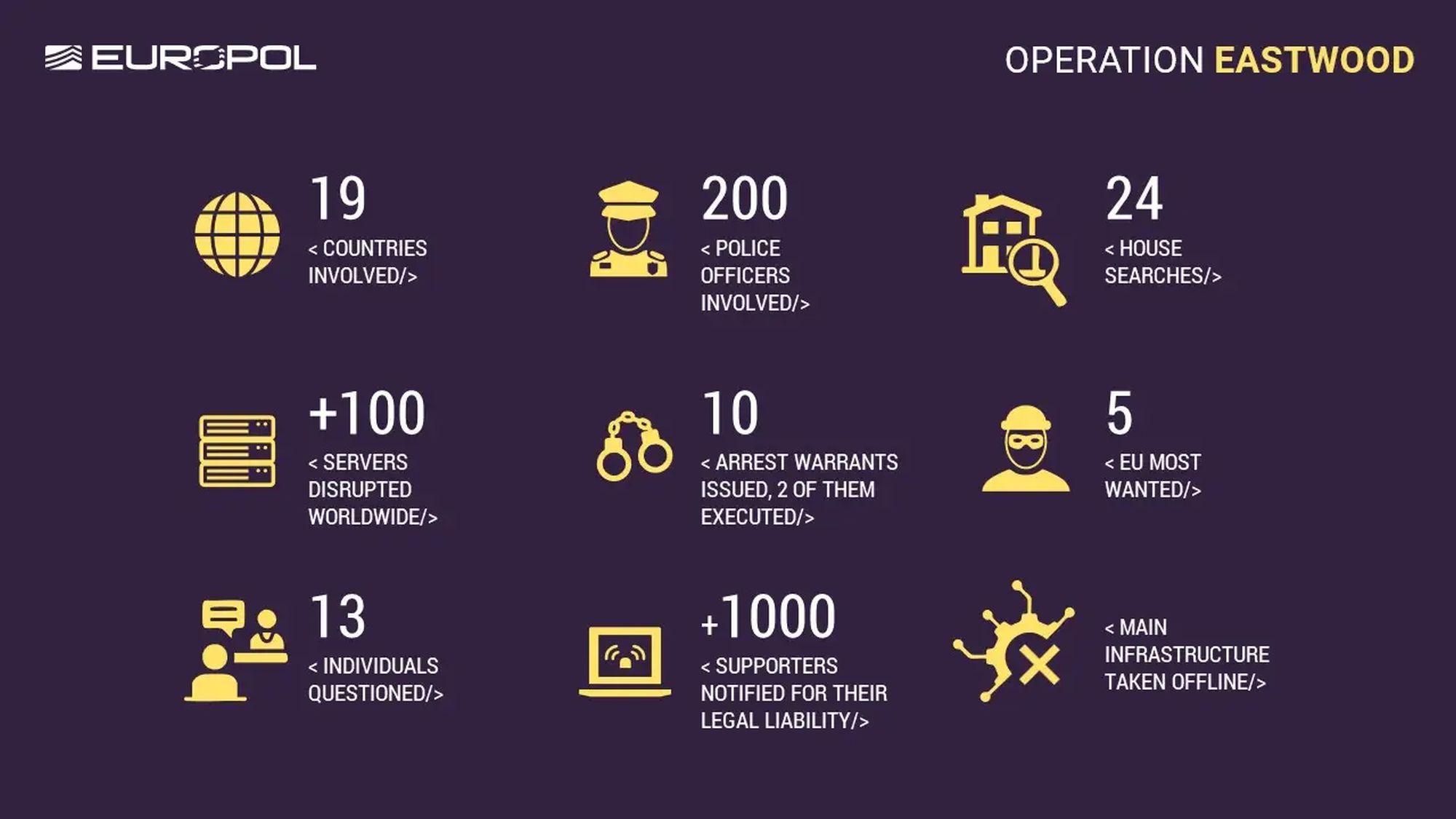
Concrete results and harm to infrastructure
As a consequence of the operation, the attacking infrastructure consisting of more than a 100 computer systems worldwide was neutralized and a crucial part of the group's central servers were shut down.
W Germany has issued six arrest warrants against Russian citizens, 2 of whom are suspected of being the main organizers of the group's activities. In total, 2 arrests were made worldwide (in France and Spain), 24 searches were conducted (including 1 in Poland) and 13 people were interviewed (including 1 in Poland). In addition, more than a 1000 people supporting the group received an online communicator notification of their criminal liability.
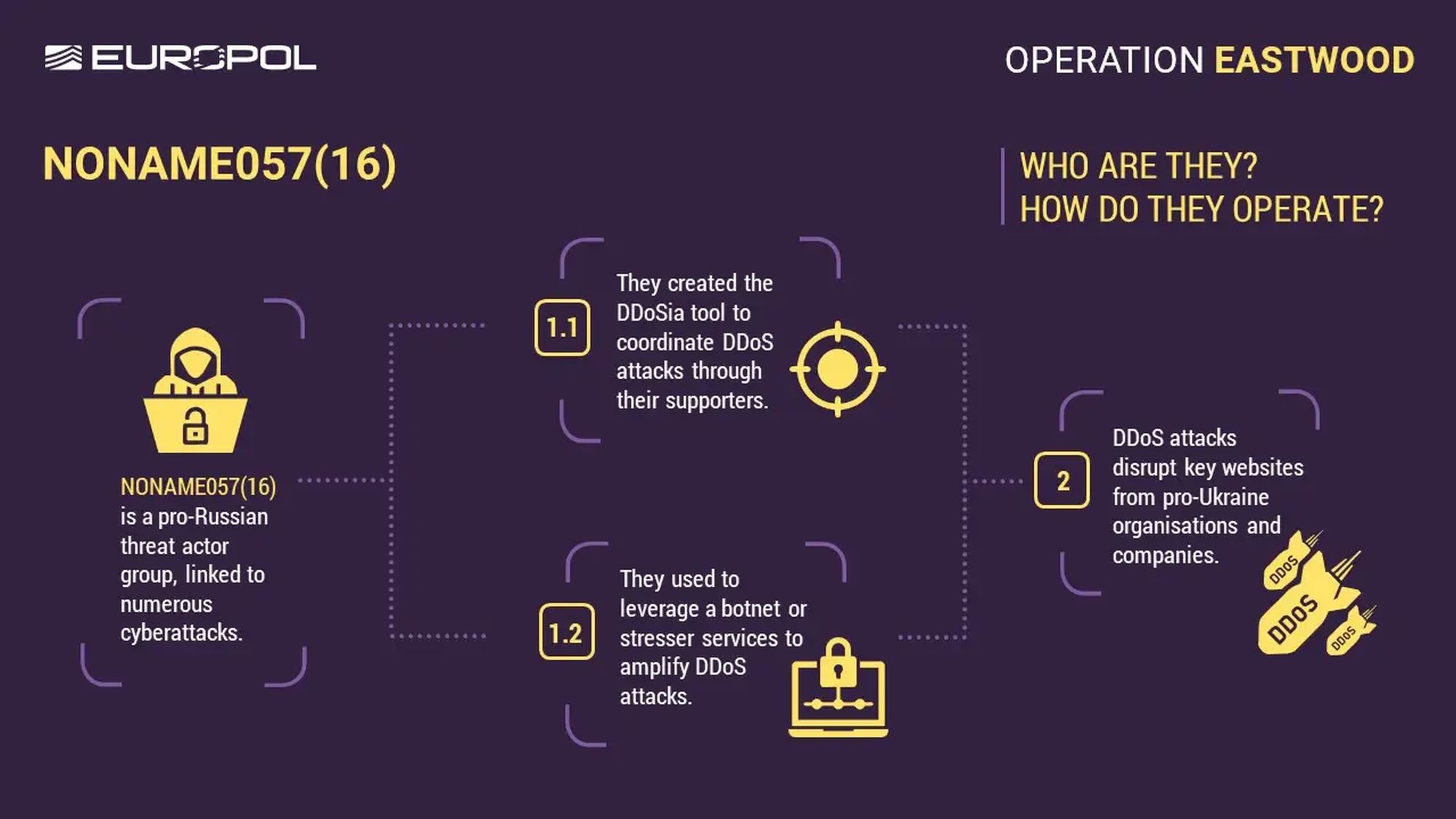
Hackers' objectives and methods
The NoName057(16) Group initially focused its attacks on targets in Ukraine, but over time it shifted its attention to NATO associate States and the European Union, which supported Kiev. The documented incidents included attacks on Swedish government institutions and banks, over 250 companies in Germany, as well as network infrastructure in Switzerland during the peace summit of June 2024 and the Netherlands during the last NATO summit. These attacks, involving flooding servers with a immense number of queries, were repulsed without causing major interference.

Investigations showed that the grid operated on the basis of sympathizers utilizing mainly Russian language, who did not have advanced method skills. The group recruited volunteers through channels in social media and communicators, motivating them with ideology, but besides prizes in cryptocurrency. The activities of NoName057(16) were marked by gaming – rankings were created, badges were awarded and the most active participants were publically praised, in order to encourage, especially younger people, regular participation in cyber attacks.
There's a fresh DDoS attack record. The servers were flooded with a wave of 7.3 Tbps garbage traffic
If article Operation Eastwood: global service broke up pro-Russian hacker network does not look right in your RSS reader, then see it on iMagazine.